iPhone 3G unlock released

As promised, the iphone-dev team has released yellowsn0w. You can install/uninstall via Cydia. It works fine with the latest firmware too. This sentence is filler.

Pouring a beer via iPhone
[Steve] sent us his new years project, a remote beer server controlled by his iPhone. He has built a frame from construx and used ioBridge to connect it to his iPhone. He states that he “wanted to make a project that allows for the perfect pour and take out all of that physical work”. Seems like it could use a little adjustment to be a bit less foamy. Maybe an additional frame to adjust the angle of the glass as it is poured.

Hacking the MyVu
[Conundrum] shares with us his MyVu hacking experiences. The MyVu personal display seems like it would be a great foundation to build some decent 3d display goggles, it is fairly small and has a screen for each eye. This opens up the door to possibly driving them independently for 3d. Those giant helmets we used to use were not anywhere near as stylish as these. Apparently, some quick hacking can double your resolution or even possibly supply 3D imagery! The details are pretty sparse, but it appears as though he has gotten some of these mods functional and tested. Lets hope he posts some more information, we’re definitely interested. We normally wouldn’t post something with so little information, but we’re hoping this encourages him to give us more.
[thanks andre]

Laughing Man in Processing

The Laughing Man is the antagonist from the anime series Ghost in the Shell: Stand Alone Complex. During each of his public appearances in the series he manages to hack all video feeds/cyborg eyes in the vicinity to obscure his face with the logo above.
[Ben Kurtz] had been watching the series recently and realized he could put together a similar effect using Processing. The interesting bit, and what makes this more fun than a simple demo, is that he’s using the OpenCV library. OpenCV is a open source computer vision library. [Ben] uses it to handle the facial recognition in Processing and then apply the image.
It’s only 100 lines and we wonder what other fun tricks could be employed. Here’s a Hack a Day skull you can swap in for the logo.
[thanks dakami]

SNES cartridge wallet

[gamemaster87] put together this SNES wallet. It isn’t just a wallet, it also has internal lighting and theme music. He harvested LEDs from Christmas lights, switches and battery compartments from an old all in one joystick, and the sounds from a holiday card. There’s a Plexiglas window to show off his ID and a belt clip, because you wouldn’t want this thing in your back pocket. Match this up with the SNES clock, NES bike tail light, and the NES security system and you’ll be the king of the nintendorks.

Home made Macintosh for under $240

[Steve] sent in this great step by step writeup on how to load Macintosh OSX onto an MSI wind. The MSI wind can be found pretty cheap, roughly $140. It has a 1.2Ghz Atom processor, SATA, and 6 USB ports. Its a pretty decent system for the price. Add a hard drive, DVD ROM and some RAM and you ‘ve got a complete system. You might have to update the bios to install the new operating system, there are more details about that on in the writeup. The only real drawback is that you have to run the USB in 12mbps mode instead of 480mbps.
There are lots of little tips to keep you from hitting roadblocks, so follow the steps closely or you’ll have to redo it. Since downloading the modified version of OSX is probably illegal, [steve] suggests that you go buy a copy of OSX just to try to balance it out.

Refillable CO2 cartridges

For those who use these little cartridges, you know how quickly the price can add up. [steve] takes us through the process of adding a valve to a spent cartridge so it can be refilled. Over all, it doesn’t seem too difficult, and [steve] offers lots of tips to increase longevity and reliability. It isn’t very often that we show a hack here that doesn’t involve some kind of electronics, so take a break from the resistors and microprocessors for a moment and enjoy.
[thanks Wolf]

Quick robotic base for netbook

This is a great example of how marketing should be done. TeleToyland and RoboRealm(currently down) have teamed up together to show you how to build a quick and easy robot base for your netbook. The build process is fairly in depth, including part numbers and links to various places to buy them. They are using RoboRealm software to control the robot, utilizing two web cams for sensory input. This should get you well on your way to having an autonomous netbook wandering around your house.

Jacob's Ladder
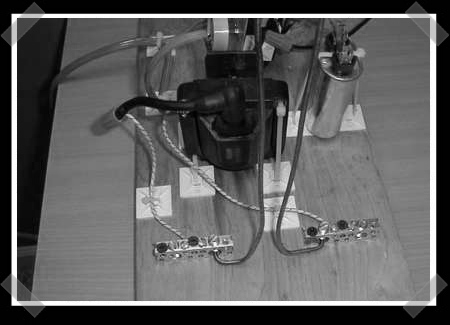
[jandgse812] shows us how to build a Jacob’s Ladder from mostly household parts. The bulk of the instructions for this project are included in the downloadable document, there is a downloadable video as well. Be sure to follow to the end where he shows us a much safer and possibly better looking revision. The Jacob’s Ladder has become standard fair for any mad scientists laboratory. If you plan on having a workshop suited for world domination, it absolutely must have one of these in it. Be careful though, the high voltage can be deadly.

25C3: Nokia exploit stops all inbound SMS

[Tobias Engel] released a serious Nokia vulnerability today. By using a specially crafted SMS message, you can block the recipient from getting any future SMS messages. The attacker changes their Protocol Identifier to “Internet Electronic Mail” and then uses any email address 32 characters or more in their message. The recipient will receive no indication that they got the message and no other messages will be allowed until the phone is factory reset. You can see a demo video here. This affects many different varieties of S60 phones and no fix is known.
[Thanks fh]

25C3: Cheap swarm robotics

The Formica project was our favorite presentation at 25C3. The goal is to build open source swarm robots as cheaply as possible. The team ended up building 25 robots in an assembly line fashion. With enough lead time, the price could get as low as £15 each. Each bot has two direct drive cellphone vibration motors with tiny neoprene wheels. They’re controlled by an MSP430 microcontroller. The only really specialized chip is a charge controller so the bots can charge without any intervention. They have copper skis on the front that touch the ground plane plus antennas to contact Vcc. On top of the bot are three IR detectors for both navigation and for transferring firmware updates between bots. A reflective sensor is on the underside for detecting “food”. It looks like a great design and any easy way for anyone to start researching swarm robotics.

25C3: Hackers completely break SSL using 200 PS3s

A team of security researchers and academics has broken a core piece of internet technology. They made their work public at the 25th Chaos Communication Congress in Berlin today. The team was able to create a rogue certificate authority and use it to issue valid SSL certificates for any site they want. The user would have no indication that their HTTPS connection was being monitored/modified.
This attack is possible because of a flaw in MD5. MD5 is a hashing algorithm; each unique file has a unique hash. In 2004, a team of Chinese researchers demonstrated creating two different files that had the same MD5 hash. In 2007, another team showed theoretical attacks that took advantage of these collisions. The team focused on SSL certificates signed with MD5 for their exploit.
The first step was doing some broad scans to see what certificate authorities (CA) were issuing MD5 signed certs. They collected 30K certs from Firefox trusted CAs. 9K of them were MD5 signed. 97% of those came from RapidSSL.
Having selected their target, the team needed to generate their rogue certificate to transfer the signature to. They employed the processing power of 200 Playstation 3s to get the job done. For this task, it’s the equivalent of 8000 standard CPU cores or $20K of Amazon EC2 time. The task takes ~1-2 days to calculate. The tricky part was knowing the content of the certificate that would be issued by RapidSSL. They needed to predict two variables: the serial number and the timestamp. RapidSSL’s serial numbers were all sequential. From testing, they knew that RapidSSL would always sign six seconds after the order was acknowledged. Knowing these two facts they were able to generate a certificate in advance and then purchase the exact certificate they wanted. They’d purchase certificates to advance the serial number and then buy on the exact time they calculated.
The cert was issued to their particular domain, but since they controlled the content, they changed the flags to make themselves an intermediate certificate authority. That gave them authority to issue any certificate they wanted. All of these ‘valid’ certs were signed using SHA-1.
If you set your clock back to before August 2004, you can try out their live demo site. This time is just a security measure for the example and this would work identically with a certificate that hasn’t expired. There’s a project site and a much more detailed writeup than this.
To fix this vulnerability, all CAs are now using SHA-1 for signing and Microsoft and Firefox will be blacklisting the team’s rogue CA in their browser products.

Card shuffling machine failure

Breaking from his usually routine of winning at everything, [Glacial Wanderer] has posted one of his projects that didn’t actually work. It’s a Rube Goldberg style card shuffling machine. He wanted something that was visually interesting while still randomizing the cards. A blower would be mounted to the top to mix the cards similar to a lottery ball machine. The cards would then drop into a chute that would make sure all of the cards were oriented correctly before being presented to the user. After building the first prototype, several problems were apparent. The first of which was the fan not being strong enough. His interest was waning and it looked like the time he’d have to invest in fixes was growing quickly, so he decided to cut his loses. He still posted about the prototype in hopes that it could help someone else exploring this sort of machine. A video of the mechanism can be found below.

25C3: CTF dominated by iphone-dev team, HackMii
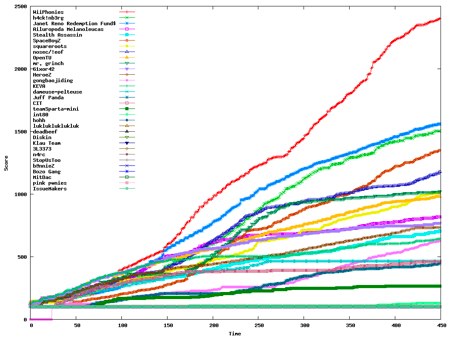
While we had been excited about 25C3’s CTF competition, we couldn’t even venture a guess as to who would win. It seems the iphone-dev team weren’t satisfied to just give an amazing talk. They teamed up with the Wii hackers from HackMii to win the competition. You can see their progress during the eight hour competition above in red. It’s impressive to see hardware hackers jumping over to network security AND completely killing at it.

You received this email because you are subscribed to the real_time feed for http://hackaday.com/feed/. To change your subscription settings, please log into RSSFWD.

