Pandora case prototype
The last time we checked in on Pandora it was just being shown in dev unit form. Embedded above is a video of the first case prototype. It doesn’t have any components yet, but it definitely looks like a good formfactor with a lot of potential. The Pandora is a Linux based portable game console with an 800×480 touchscreen.
[via Gizmodo]

wireless bootloading
Tired of having to physically connect to your microprocessor to upload new code? Just do it over a wireless connection. [Nathan] takes us through the process of setting up a wireless bootloader for the ATmega168. He is using the XBee base and remote modules for the wireless communication. While people have been doing wireless bootloading with the Arduino already, [Nathan] found that it was common for them to have timeout issues. His remedy was to make his own custom one that is much faster. He’s asking for help though. At this point it is tested and working, but he needs someone with more programming knowledge to help him make it “drop-in” compatible with the Arduino IDE.
Don’t forget to submit projects to our tip line.

5 cent tilt sensor
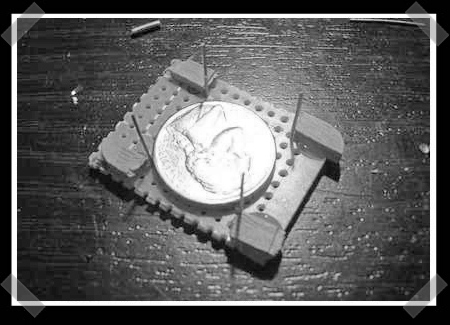
This is a 5 cent tilt sensor. We know it cost more than 5 cents, but it is in fact a tilt sensor that utilizes a 5 cent coin. We’ve all done quick hacks to make quick sensors for various projects. We’ve seen tons of them, from stealing springs out of pens and shoving a resistor through them for flexible contact switches, to tin foil touch sensors. This one is new to us though. The design is fairly simple, you insert 4 bits of wire to serve as contacts and the coin will make contact with only two at a time. It isn’t analog, it isn’t extremely precise, but it is super quick and easy. Thanks for sharing [ix].

Quake on the BUG
It seems like every piece of hardware has to earn its respect by going through some standard paces. One of which is having Quake ported to it. Much like an angel earning their wings, Bug Labs, with the help of community [CMW], has ported quake to the BUG. Right now, the only add on needed is the BugView module. Controls are done through the base unit.

Thermosonic wedge bonding
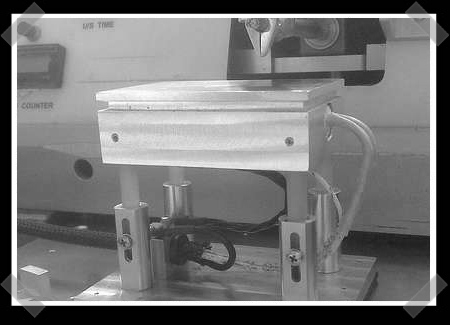
In the past, if we’ve been doing smd soldering, we’ve used pretty basic hot plates. This project takes that idea a bit further. Since [kc6qhp] will be using parts that aren’t conducive to soldering, he has to use wire bonding. After locating a fairly cheap wire bonding machine and microscope, he built the heated stage to fit perfectly with his other tools. You’ll notice that he has machined a lip around the heat plate for small custom C-clamps as well as made it adjustable height. Very nice work [kc6qhp].

Portable Wii

Not content with Nintendo’s current portable video game offerings, fifteen year old hardware hacker [Xteaphn] (pronounced “Steven”) has come up with a series of hardware modifications to make a battery-operated Wii console. The hacked console features a folding laptop-like screen, which apparently includes the IR emitters necessary to make the Wiimote operate properly, as well as a set of tiny stereo speakers. To show how tiny the modified console is, [Xteaphn] provides size comparisons with thirteen- and fifteen-inch laptops as well as with a classic Nintendo Game Boy. The only potential hindrance to its long-term durability, as best as we can tell from the video, is that the battery pack and its associated connecting wires hang crudely off the back of the console like a sort of electric colostomy bag.
Check out [Xteaphn]’s YouTube video after the break.
[via Engadget]

Sweat bot

The future is here ladies and gentlemen, robots are truly making our lives better. The grueling job of sweating into clothing has been taken over by the latest in technology: the sweat bot. With water heated fake skin, and robotic sweat glands, this machine works tirelessly to test clothing. While emulating walking or jogging, it sweats into the clothing. This helps in the design of more breathable and sweat resistant fabrics. Though we know it is just a machine, choosing to put the water hoses through its face was just plain creepy.
[via BotJunkie]

Ferric chloride etching chemistry

[ladyada] has republished an interesting snippet from the synthDIY mailing list. [David Dixon] discusses the actual chemistry behind ferric chloride based home circuit board etching. He concludes that ferric chloride is essentially a ‘one-shot’ oxidant. It can’t be regenerated and can be difficult to dispose of properly. The use of acidified copper chloride is a much better path and becomes more effective with each use, as long as you keep it aerated and top up the acidity from time to time. This etchant solution is actually the result of initially using hydrogen peroxide as an oxidant along with muriatic acid. You can see us using this solution in our etching how-to and while creating the board for our RGB lock. For more information on using hydrogen peroxide, check out [Adam Seychell]’s guide and this Instructable.
Aside: [ladyada] has added the receiver code to the Wattcher project page.

Besmoke - fluid dynamics
Besmoke is a fluid dynamics engine. It is compatible with any multitouch system, as well as the accelerometer in an iPhone. It also accepts audio input. The audio input can turn it into a fancy music visualizer that would even work with live or acoustic music. Different frequencies cause fluid to be injected from different “emitters”. There’s great info on his page, including the papers that he based this off of. We’ve covered [Eric]’s work before with his election party light system.

Autofocus assist light
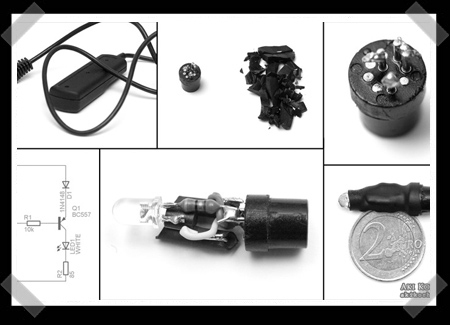
[Aki]’s Nikon D2H did not come with an autofocus assist light. His other cameras have them, and he likes the feature, so he decided to hack one into his D2H. He wired into the AF system, so that his LED gets voltage when the shutter release is pressed half way. The circuit needs refinement though, he found that the light was staying on during shutter release and affecting his light metering. You can see the hack in action after the break.

Parts: AT keyboard

Last week we introduced a new version of the Bus Pirate universal serial interface tool. The last firmware update included an AT keyboard decoder library for both hardware versions.
There’s a ton of old AT keyboards making their way to the landfill. We’ll show you how to recycle one as an input device for your next project.
Connection
| Bus Pirate | PC AT keyboard (pin #) |
| SDA | KBD Data (3) |
| SCL | KBD Clock (1) |
| +5volts | VDD (5) |
| GND | GND (2) |
AT keyboards communicate over a bidirectional two-wire interface. The bus is open collector, but keyboards already have internal pull-up resistors. The PC AT keyboard protocol is described here. We used our Bus Pirate tool to demonstrate the keyboard protocol, but the same basic principals apply to any microcontroller.
We connected the Bus Pirate to the keyboard as outlined in the table. We believe that this is a through-hole female AT keyboard jack, but we haven’t tested it. Do you know of a source for new sockets?
Protocol
The keyboard provides the clock signal for all data transfers; the PC side resembles a slave device. None of the existing Bus Pirate interface libraries work with an external clock, so we wrote a simple AT keyboard decoder library. The library depends on the keyboard’s clock signal, and it’ll hang if the keyboard fails or isn’t connected. If you use our library in your own project, consider adding a timeout delay in the readbit() and writebit() functions.
PC to keyboard command codes
| Code | Command |
| 0xed | Set status LEDs |
| 0xee | Echo 0xee |
| 0xf0 | Set scancode type |
| 0xf3 | Set repeat rate |
| 0xf4 | Keyboard enable |
| 0xf5 | Keyboard disable |
| 0xfe | Resend last byte |
| 0xff | Reset keyboard |
A PC uses these commands to control various functions of an AT keyboard. The keyboard responds to commands with an acknowledge byte (oxfa). In our experience, the keyboard will reset if the response byte is not read shortly after the command is sent.
Keyboard to PC response codes
| Code | Response |
| 0xfa | Acknowledge |
| 0xaa | Self test passed |
| 0xee | Echo response |
| 0xfe | Resend last byte |
| 0×00 or 0xff | Error or buffer overflow |
The keyboard has a number of single byte response codes. Most PC commands are acknowledged with 0xfa. 0xaa is sent after a keyboard reset.
Setup the Bus Pirate
HiZ>m
1. HiZ
…
9. PC AT KEYBOARD
MODE>9 <–set mode
900 MODE SET
X02 PC AT KB DECODER READY
PC AT KEYBOARD>
First, we setup the the Bus Pirate for AT keyboard mode, option 9.
PC AT KEYBOARD>p <–power supply setup
W/w toggles 3.3volt supply?
1. NO
2. YES
MODE>1 <–no 3.3volt supply
W/w toggles 5volt supply?
1. NO
2. YES
MODE>2 <–use the 5volt supply
9xx SUPPLY CONFIGURED, USE W/w TO TOGGLE
9xx VOLTAGE MONITOR: 5V: 0.0 | 3.3V: 0.0 | VPULLUP: 0.0 |
PC AT KEYBOARD>W <–capital ‘W’, turn supply on
9xx 5VOLT SUPPLY ON
PC AT KEYBOARD>
Next, we configure the Bus Pirate’s power supply to provide 5volts for the AT keyboard.
PC AT KEYBOARD>r <–read byte from keyboard
x30 PCATKB READ: NONE <–no data available
PC AT KEYBOARD>
The AT keyboard library follows the standard Bus Pirate syntax. Numeric values are sent to the keyboard as bytes, ‘r’ reads a byte from the keyboard. The protocol is clocked by the keyboard so bitwise operations are disabled. If no data is available, the read will return ‘NONE’.
Setup the keyboard
PC AT KEYBOARD>0xee r <–send 0xee, read one byte
X20 PCATKB WRITE: 0xEE GOT ACK <–write oxee, got ack bit
x30 PCATKB READ: 0xEE <–read 0xee, echo was successful
PC AT KEYBOARD>
We can test the connection to the AT keyboard using the echo command, 0xee. The keyboard will respond 0xee if our connections are correct.
The keyboard responds to commands with an ACK bit at the protocol level, and then again with an ACK byte. We found that our test keyboards reset automatically if the ACK byte wasn’t read immediately after sending the command.
PC AT KEYBOARD>0xee <–echo command
X20 PCATKB WRITE: 0xEE GOT ACK <–wrote echo, got ACK
PC AT KEYBOARD>r <–read one byte
x30 PCATKB READ: 0xAA <–read 0xaa, reset indicator
PC AT KEYBOARD>
Here, we tried to send the echo command and then read the reply later. The keyboard reset automatically and replies 0xaa, self-test passed.
PC AT KEYBOARD>0xff r r <–reset command, read two bytes
X20 PCATKB WRITE: 0xFF GOT ACK <–write reset command, got ACK
x30 PCATKB READ: 0xFA <–command ACK byte
x30 PCATKB READ: NONE <–read once more to reset
PC AT KEYBOARD>
The keyboard is reset by writing the command 0xff, and reading two bytes. The Keyboard won’t reset until the second byte is read.
PC AT KEYBOARD>r <–read a byte
x30 PCATKB READ: 0xAA <–reset success
PC AT KEYBOARD>
A short period after reset we can read the power on self test (POST) results, 0xaa indicates POST success.
PC AT KEYBOARD>0xf5 r <–disable the keyboard
X20 PCATKB WRITE: 0xF5 GOT ACK <–wrote command
x30 PCATKB READ: 0xFA <–read ACK byte
PC AT KEYBOARD>0xf4 r <–enable keyboard
X20 PCATKB WRITE: 0xF4 GOT ACK <–wrote command
x30 PCATKB READ: 0xFA <–read ACK byte
PC AT KEYBOARD>
0xf5 disables keyboard input. 0xf4 enables the keyboard and clears the buffer.
PC AT KEYBOARD>0xed r 0b111 r <–set indicator LEDs
X20 PCATKB WRITE: 0xED GOT ACK <–set LED command
x30 PCATKB READ: 0xFA <–command acknowledged
X20 PCATKB WRITE: 0×07 GOT ACK <–send LED value
x30 PCATKB READ: 0xFA <–value acknowledged
PC AT KEYBOARD>
The num, caps, and scroll lock LEDs are controlled by the 0xed command. The last three bits of a second byte (ob111) indicate which LEDs to light. It’s very important to perform all four byte operations within the keyboard timeout period, or the keyboard will reset.
PC AT KEYBOARD>0xee r <–echo test command
X20 PCATKB WRITE: 0xEE GOT ACK
x30 PCATKB READ: 0xEE
PC AT KEYBOARD>0xfe r <–repeat last byte command
X20 PCATKB WRITE: 0xFE GOT ACK <–write repeat command
x30 PCATKB READ: 0xEE <–previous byte is repeated
PC AT KEYBOARD>
The last interesting keyboard command is the repeat byte command. 0xfe causes the keyboard to send the last byte again. This is a useful command if there was a error in the previous transmission.
Read key presses
Key presses are buffered by the keyboard until we read them.
PC AT KEYBOARD>r <–read byte
x30 PCATKB READ: 0×29 <–space scancode
PC AT KEYBOARD>r <–read byte
x30 PCATKB READ: 0xF0 <–key release scancode
PC AT KEYBOARD>r <–read byte
x30 PCATKB READ: 0×29<–space scancode
PC AT KEYBOARD>
A key press sends scancodes, multi-byte sequences that represent the key presses. In the example, we pressed space which has the scancode 0×29. When a key is released, the keyboard sends 0xf0 and the scancode for the key (0×29). Each key press results in a similar three part sequence.
PC AT KEYBOARD>r:4 <–read 4 bytes
x31 PCATKB BULK READ, 0×04 BYTES:
0×29 0xF0 0×29 NONE <–space scancode
PC AT KEYBOARD>
This is just a simplified version of the previous example. Rather than read three bytes individually, we used the bulk read command. Again, we get the space scancode sequence. Our attempt to read a non-existant fourth byte fails.

Forknife, Android G1 controlled robot

When we first saw [Jeffrey Nelson]’s G1 based robot we immediately wondered what the transport for the controls was. The G1’s hardware supports USB On-The-Go, but it’s not implemented in Android yet. It turns out he’s actually sending commands by using DTMF tones through the headphone adapter. The audio jack is connected to a DTMF decoder that sends signals to the bot’s Arduino. He wrote client/server code in Java to issue commands to the robot. You can find that code plus a simple schematic on his site. A video of the bot is embedded below.
[via Engadget]

TEMPEST: A Signal Problem

TEMPEST is the covername used by the NSA and other agencies to talk about emissions from computing machinery that can divulge what the equipment is processing. We’ve covered a few projects in the past that specifically intercept EM radiation. TEMPEST for Eliza can transmit via AM using a CRT monitor, and just last Fall a group showed how to monitor USB keyboards remotely. Through the Freedom of Information Act, an interesting article from 1972 has been released. TEMPEST: A Signal Problem (PDF) covers the early history of how this phenomenon was discovered. Uncovered by Bell Labs in WWII, it affected a piece of encryption gear they were supplying to the military. The plaintext could be read over that air and also by monitoring spikes on the powerlines. Their new, heavily shielded and line filtered version of the device was rejected by the military who simply told commanders to monitor a 100 feet around their post to prevent eavesdropping. It’s an interesting read and also covers acoustic monitoring. This is just the US history of TEMPEST though, but from the anecdotes it sounds like their enemies were not just keeping pace but were also better informed.
[via Schneier]

Sound effects box

At first glance, this may look like a retro styled monome, but it is actually quite different. Merging a Project64 key pad and a Voice Shield for Arduino, [Spikenzie] has made a sound effects box. Each button triggers a unique sound that is stored in the Voice Shield. Of coarse, it will be like a game of memory trying to remember what sound is where. You can see a demo video here.

Wattcher, twittering Kill A Watt plans posted

You probably saw [Phillip Torrone] and [Limor Fried]’s twittering Kill A Watt earlier this week. It was an entry in the Core77/Greener Gadgets Design Competition. We saw a little bit about how it was assembled, but now they’ve posted a full guide to assembling the hardware. Each Kill A Watt gets an XBee radio that transmits back to a receiver that logs the power usage. The difficult part when putting this design together was the XBee required 50mA when transmitting. This is well above the Kill A Watt’s internal power supply. They remedied this by adding a 10,000uF supercap to act as a rechargeable battery. The daily twittering is just a side-effect of the project. The Kill A Watts transmit every 2 seconds, so you’ll get a very accurate report of your power usage. This is a great project for renters who can’t permanently modify their power infrastructure. Each Kill A Watt can support quite a few appliances since they’re rated for 15A, ~1800W.

You received this email because you are subscribed to the real_time feed for http://hackaday.com/feed/. To change your subscription settings, please log into RSSFWD.





No comments:
Post a Comment